Windows Defender: The Unsung Hero Of Windows 10 Security
Windows Defender: The Unsung Hero of Windows 10 Security
Related Articles: Windows Defender: The Unsung Hero of Windows 10 Security
Introduction
With great pleasure, we will explore the intriguing topic related to Windows Defender: The Unsung Hero of Windows 10 Security. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Windows Defender: The Unsung Hero of Windows 10 Security

Windows 10, a ubiquitous operating system powering millions of devices, comes equipped with a robust built-in security solution: Windows Defender. Often overshadowed by third-party antivirus software, Windows Defender plays a critical role in safeguarding Windows 10 users from the ever-evolving threat landscape of malware, viruses, and other cyber threats.
This article delves into the intricacies of Windows Defender, exploring its functionalities, benefits, and limitations, providing a comprehensive understanding of this essential security component.
Understanding Windows Defender: A Multi-Layered Security Approach
Windows Defender is not simply an antivirus program; it encompasses a suite of security features designed to provide a comprehensive defense against various threats. Its core functionalities include:
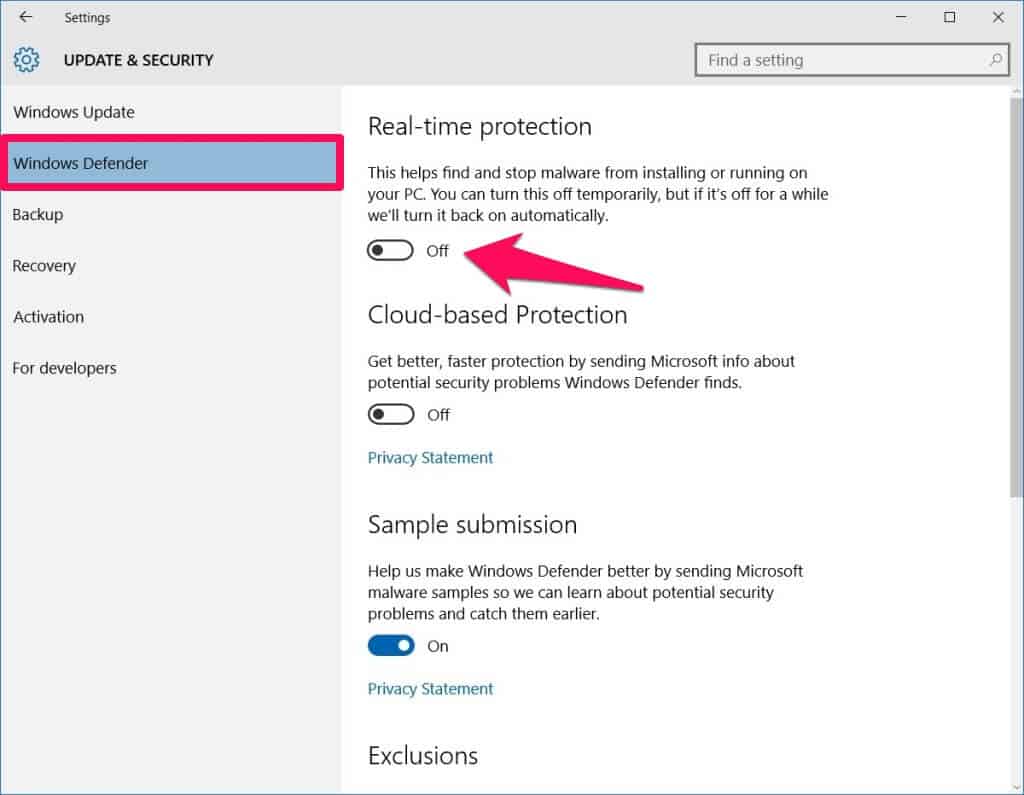
- Real-time Protection: Windows Defender constantly monitors the system for suspicious activities, proactively blocking malicious software from gaining access or executing harmful code. This includes scanning files downloaded from the internet, email attachments, and even USB drives.
- On-demand Scans: Users can initiate full system scans or target specific folders and files for malware detection. These scans are particularly useful for addressing potential infections or ensuring a clean system before connecting to a network.
- Cloud-powered Protection: Windows Defender leverages Microsoft’s cloud infrastructure to enhance its detection capabilities. Suspicious files are analyzed in the cloud, utilizing a vast database of known threats and machine learning algorithms to identify previously unknown malware.
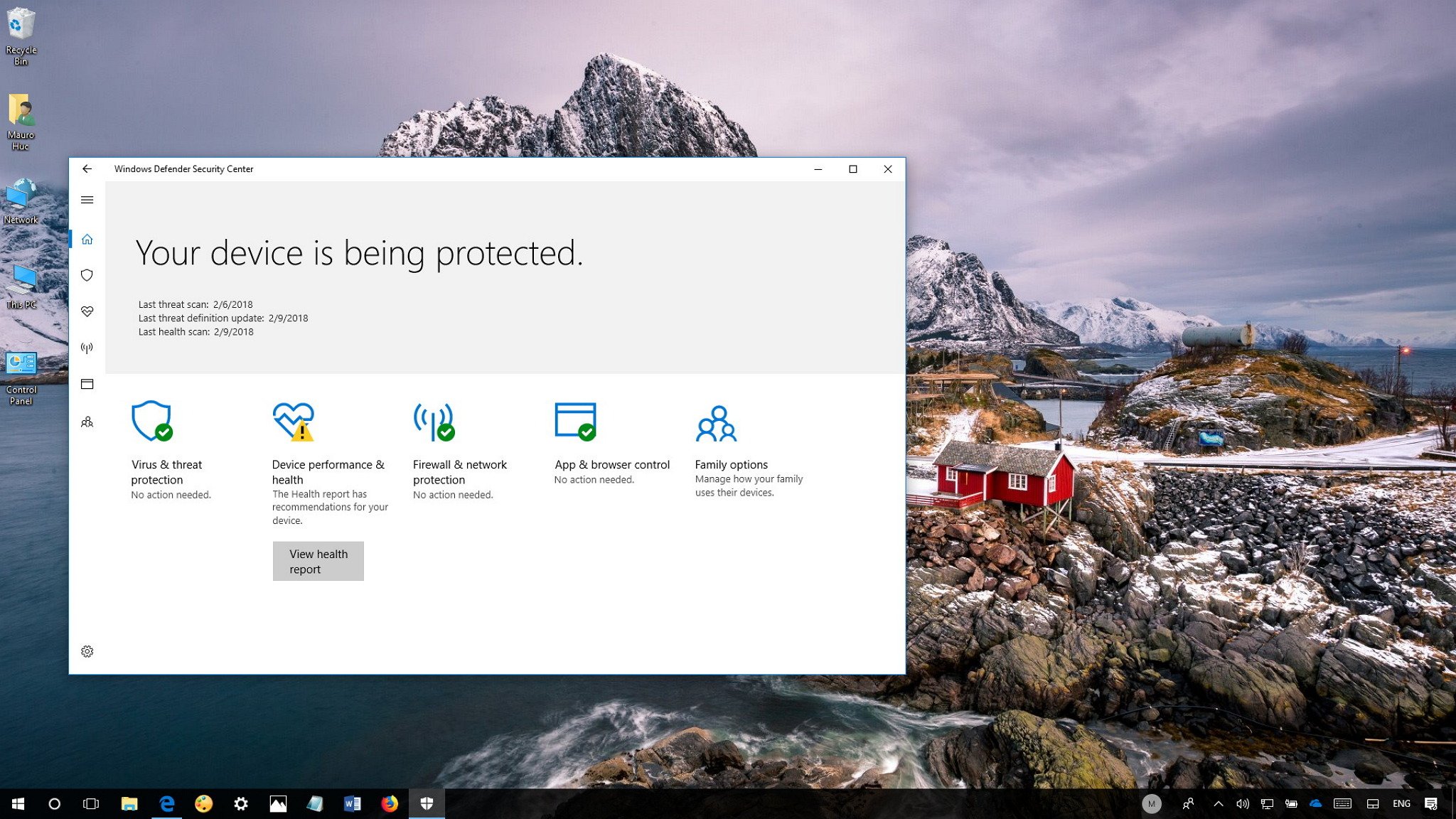
- Firewall: Windows Defender Firewall acts as a barrier between the system and the outside world, controlling incoming and outgoing network traffic. This feature helps prevent unauthorized access to the system and protects against potential attacks targeting network vulnerabilities.
- Exploit Protection: Windows Defender’s exploit protection feature aims to mitigate vulnerabilities in software applications that can be exploited by attackers. It employs various techniques, such as preventing malicious code from executing in memory or modifying system settings.
- Anti-phishing: Windows Defender’s anti-phishing capabilities help protect users from websites designed to steal personal information, such as login credentials and financial details. It analyzes websites and flags suspicious activities, alerting users to potential threats.
- App Control: Windows Defender’s app control feature allows users to restrict the execution of specific applications, ensuring that only trusted programs can run on the system. This helps prevent malware from gaining a foothold by masquerading as legitimate software.
Benefits of Windows Defender: A Robust and Reliable Security Solution
While the concept of "free" security software might raise concerns, Windows Defender offers several advantages that make it a compelling choice for Windows 10 users:
- Built-in Security: Windows Defender is seamlessly integrated into Windows 10, eliminating the need for separate installations and reducing the potential for compatibility issues. This streamlined approach ensures that security is always active and readily available.
- Automatic Updates: Windows Defender receives automatic updates, ensuring that its threat detection database and security features are always up-to-date. This eliminates the need for manual updates and ensures protection against the latest threats.
- Lightweight Performance: Windows Defender is designed to be efficient and consume minimal system resources, minimizing performance impact on the device. This is particularly beneficial for users with limited system resources or those who prioritize performance.
- User-friendly Interface: Windows Defender’s user interface is intuitive and straightforward, making it easy for users of all skill levels to navigate and manage its settings.
- Comprehensive Protection: Windows Defender’s multi-layered approach offers a robust defense against various threats, including malware, viruses, ransomware, and phishing attacks. This comprehensive protection ensures a secure environment for users.
Limitations of Windows Defender: Addressing Potential Concerns
While Windows Defender offers a powerful security solution, it’s crucial to acknowledge its limitations:
- Limited Customization: Windows Defender provides a basic level of customization, but some users may desire more advanced features or granular control over specific settings. This limitation can be addressed by exploring third-party security solutions that offer a wider range of customization options.
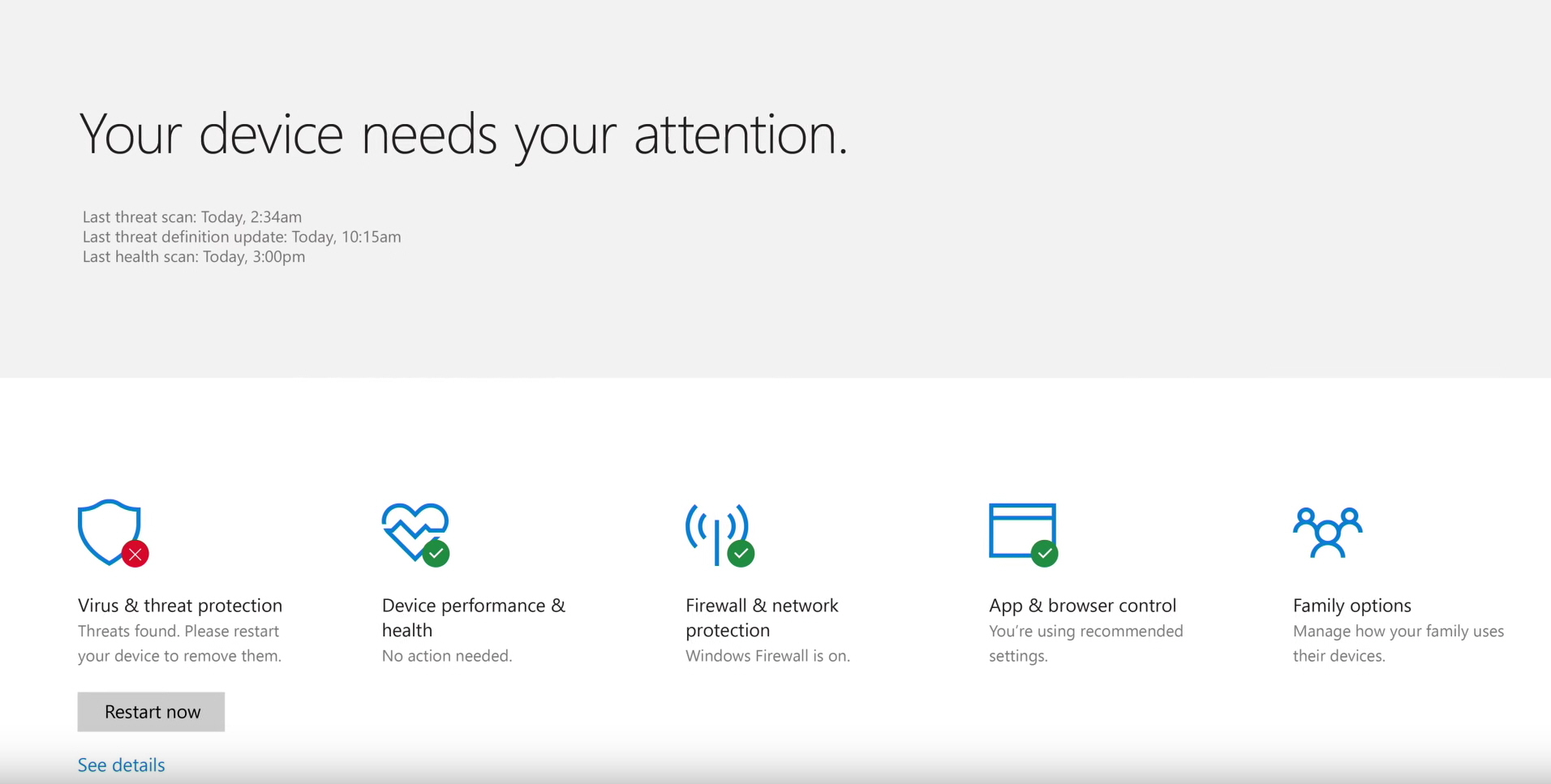
- Potential for False Positives: Although Windows Defender’s threat detection capabilities are constantly improving, it can occasionally flag legitimate programs or files as malicious. This is known as a false positive and can disrupt user workflows. However, these incidents are becoming less frequent with advancements in machine learning and cloud-based threat analysis.
- Limited Advanced Features: While Windows Defender provides a solid foundation for security, it may lack advanced features found in premium third-party security solutions, such as anti-exploit protection, behavioral analysis, or vulnerability scanning.
FAQs About Windows Defender
1. Is Windows Defender Sufficient for Protection?
Windows Defender provides a solid foundation for security and is sufficient for many users. However, individuals with heightened security needs, such as those working with sensitive data or frequently accessing public networks, may benefit from additional protection offered by third-party security solutions.
2. Can I Use Windows Defender Alongside Third-party Antivirus Software?
It is generally not recommended to run Windows Defender alongside other antivirus software. This can lead to conflicts and performance issues. If you choose to use a third-party antivirus, disable Windows Defender to avoid conflicts.
3. How Do I Configure Windows Defender Settings?
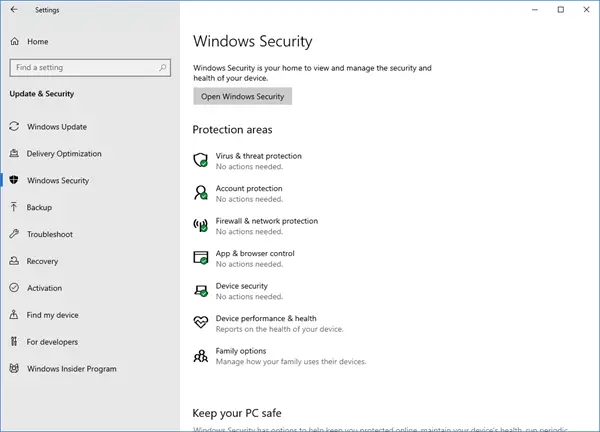
To access Windows Defender settings, open the "Windows Security" app (previously known as "Windows Defender Security Center") from the Start menu or search bar. From there, you can manage various settings, such as real-time protection, scan schedules, and exclusion lists.
4. How Do I Report a False Positive?
If you believe Windows Defender has flagged a legitimate program or file as malicious, you can report it to Microsoft. Open the "Windows Security" app, navigate to "Virus & threat protection," and select "Protection history." Locate the flagged item and click "Submit feedback."
5. How Often Should I Scan My System?
Windows Defender performs automatic scans regularly, but it’s beneficial to schedule additional scans, particularly after installing new software or visiting untrusted websites. You can set up custom scan schedules within the "Windows Security" app.
Tips for Enhancing Windows Defender’s Effectiveness
While Windows Defender offers a robust security solution, implementing best practices can further enhance its effectiveness:
- Keep Windows Updated: Regularly update your Windows operating system to receive the latest security patches and fixes. These updates address vulnerabilities that can be exploited by attackers.
- Use Strong Passwords: Employ strong, unique passwords for all your accounts, including your Windows login. Avoid using easily guessable passwords or reusing the same password across multiple accounts.
- Enable Two-factor Authentication: Whenever possible, enable two-factor authentication (2FA) for your accounts. This adds an extra layer of security by requiring a second verification step, such as a code sent to your phone or email.
- Be Cautious of Email Attachments: Exercise caution when opening email attachments, especially from unknown senders. Avoid clicking on links or opening attachments from suspicious emails.
- Avoid Visiting Untrusted Websites: Limit your visits to websites you trust and avoid clicking on suspicious links or advertisements.
- Be Wary of Phishing Attempts: Be vigilant about phishing attempts, which aim to trick users into revealing personal information. Look for suspicious emails, websites, or phone calls that request sensitive data.
- Install Software from Trusted Sources: Download software only from trusted sources, such as official websites or reputable app stores. Avoid downloading software from untrusted websites or through torrents.
- Use a Password Manager: A password manager can help you create and store strong, unique passwords for all your accounts. It can also automatically fill in login credentials, reducing the risk of human error.
- Back Up Your Data: Regularly back up your important data to an external hard drive or cloud storage service. This ensures that you can recover your data in case of a malware infection or other data loss event.
Conclusion: A Crucial Component of Windows 10 Security
Windows Defender, often overlooked, plays a crucial role in protecting Windows 10 users from cyber threats. Its multi-layered security approach, automatic updates, and user-friendly interface make it a valuable asset for users seeking a reliable and efficient security solution. While Windows Defender may have limitations, it provides a solid foundation for security and can be enhanced through best practices and the use of additional security tools. By understanding and utilizing Windows Defender effectively, users can significantly reduce their risk of falling victim to cyberattacks and maintain a secure computing environment.



Closure
Thus, we hope this article has provided valuable insights into Windows Defender: The Unsung Hero of Windows 10 Security. We thank you for taking the time to read this article. See you in our next article!