Unveiling The Trail: Understanding File Access History In Windows 10
Unveiling the Trail: Understanding File Access History in Windows 10
Related Articles: Unveiling the Trail: Understanding File Access History in Windows 10
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unveiling the Trail: Understanding File Access History in Windows 10. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Trail: Understanding File Access History in Windows 10
In the digital realm, where information flows freely and data becomes increasingly valuable, understanding who has accessed specific files is paramount. Windows 10, with its sophisticated operating system, offers a range of tools and features to monitor and track file access, providing users with valuable insights into the activity surrounding their data. This article delves into the intricacies of file access history in Windows 10, exploring the mechanisms, functionalities, and implications of this crucial feature.
The Foundation: File System Auditing
At the core of Windows 10’s file access tracking lies the concept of file system auditing. This powerful security feature allows administrators and users to monitor and record specific file system events, including file creation, deletion, modification, and access. By enabling auditing, users can create a detailed log of actions performed on their files, providing a comprehensive record of who accessed what, when, and how.
Enabling Auditing: A Step-by-Step Guide
To leverage the power of file system auditing, users must first enable it. This process involves navigating through the Windows 10 interface to configure the desired auditing settings.
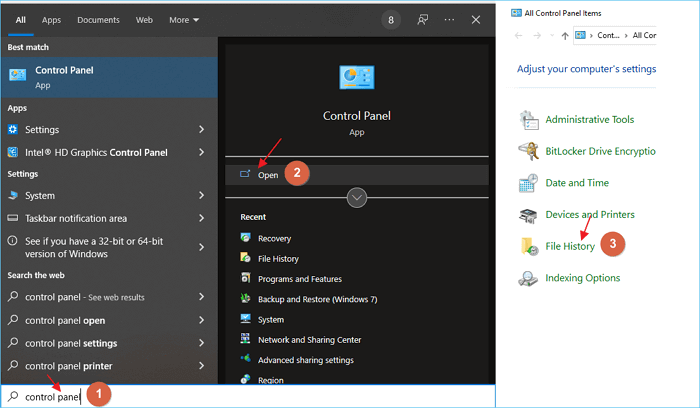
- Access the Local Group Policy Editor: This is achieved by searching for "gpedit.msc" in the Windows search bar.
- Navigate to the Appropriate Policy: Within the Local Group Policy Editor, users should locate "Computer Configuration > Windows Settings > Security Settings > Local Policies > Audit Policy."
- Select the Desired Audit Events: This section presents a comprehensive list of file system events that can be audited, including "File and Folder Access," "Object Access," and "Account Management."
- Configure Audit Settings: For each selected audit event, users can choose to "Success," "Failure," or both. This determines whether the audit log will record successful or failed attempts to access files.
Interpreting the Audit Log: A Window into File Activity
Once auditing is enabled, Windows 10 diligently records every audited file system event in the Security Event Log. This log, accessible through the Event Viewer (accessible via the search bar or by typing "eventvwr.msc"), provides a detailed chronicle of file access activities.
Analyzing the Security Event Log requires a certain level of technical understanding. Each entry contains information such as:
- Event ID: A unique identifier for the specific event, allowing for easy categorization.
- Date and Time: Precise timestamps indicating when the event occurred.
- User Account: The name of the user account responsible for the action.
- Object Name: The specific file or folder that was accessed.
- Access Type: The type of access performed, such as "Read," "Write," or "Delete."
The Importance of File Access History: Unveiling the Benefits
The ability to track file access history in Windows 10 offers a multitude of benefits, enhancing security, accountability, and troubleshooting capabilities.
- Security Enhancement: By monitoring file access, users can detect unauthorized activity and identify potential security breaches. This proactive approach helps safeguard sensitive data and mitigate risks.
- Accountability and Compliance: Tracking file access provides a clear audit trail, enabling administrators to identify individuals responsible for specific actions. This is essential for compliance with regulations and legal requirements, ensuring transparency and accountability.
- Troubleshooting and Investigation: When issues arise, the file access history can provide valuable insights into the cause of the problem. This allows for efficient troubleshooting and investigation, leading to quicker resolution of issues.
- Data Recovery: In the event of accidental file deletion or data loss, the file access history can be used to pinpoint the last known location of the file. This information can be crucial for data recovery efforts.
FAQs: Addressing Common Queries about File Access History
1. Can I track file access for specific users only?
Yes, Windows 10 allows for targeted auditing of specific user accounts. This can be achieved by configuring the audit settings for individual user accounts within the Local Group Policy Editor.
2. How long is file access history stored?
The duration of file access history storage depends on the system’s configuration. Administrators can configure the maximum size of the Security Event Log, limiting the amount of data stored. Additionally, log rotation settings can be implemented to automatically archive and overwrite older log entries.
3. Can I view the file access history for a specific file?
While the Security Event Log provides a comprehensive record of file access events, it does not directly link specific files to the events. To identify the events related to a particular file, users may need to analyze the log entries based on the file’s location and name.
4. Is file access history affected by user privileges?
Yes, user privileges play a crucial role in file access auditing. Administrators have the highest level of access and can configure auditing settings for all users. Standard users, on the other hand, have limited access and may not be able to view or modify the Security Event Log.
5. Can I export the file access history?
Yes, the Security Event Log can be exported into various formats, including CSV and XML. This allows for easy analysis and sharing of the data.
Tips for Effective File Access Monitoring
- Define Clear Auditing Policies: Establish specific guidelines for file access auditing, outlining the events to be monitored, the duration of data retention, and the procedures for accessing and interpreting the audit log.
- Regularly Review the Audit Log: Make it a practice to regularly review the Security Event Log for any suspicious activity or potential security breaches.
- Use Event Log Analysis Tools: Employ specialized tools to analyze and interpret the Security Event Log, providing insights and identifying patterns that may not be readily apparent.
- Implement Strong Access Control Policies: Supplement file access auditing with robust access control measures, such as password protection, encryption, and user account restrictions, to further enhance data security.
Conclusion: A Powerful Tool for Security and Transparency
Windows 10’s file access history functionality is a powerful tool that empowers users and administrators to monitor, track, and understand the activity surrounding their data. By leveraging this feature, users can enhance security, ensure accountability, facilitate troubleshooting, and maintain data integrity. Understanding and utilizing file access history is essential for navigating the complexities of the digital landscape, safeguarding valuable information, and maintaining a secure and transparent digital environment.
:max_bytes(150000):strip_icc()/010-how-to-use-file-history-in-windows-10-65a8020ce114471eb3f04e8ef4683ac6.jpg)

:max_bytes(150000):strip_icc()/FileHistory1-56ce0b065f9b5879cc5c3bfc.png)

Closure
Thus, we hope this article has provided valuable insights into Unveiling the Trail: Understanding File Access History in Windows 10. We hope you find this article informative and beneficial. See you in our next article!