Understanding User Activity In Windows 10: A Comprehensive Guide
Understanding User Activity in Windows 10: A Comprehensive Guide
Related Articles: Understanding User Activity in Windows 10: A Comprehensive Guide
Introduction
With great pleasure, we will explore the intriguing topic related to Understanding User Activity in Windows 10: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Understanding User Activity in Windows 10: A Comprehensive Guide
- 2 Introduction
- 3 Understanding User Activity in Windows 10: A Comprehensive Guide
- 3.1 The Importance of Tracking User Activity
- 3.2 Methods for Identifying Logged-in Users
- 3.3 Understanding User Activity: FAQs
- 3.4 Tips for Managing User Activity
- 3.5 Conclusion
- 4 Closure
Understanding User Activity in Windows 10: A Comprehensive Guide
Windows 10, like any operating system, provides a robust framework for managing user accounts and tracking their activity. This comprehensive guide aims to demystify the various methods for identifying currently logged-in users on a Windows 10 system, exploring their significance and applications.
The Importance of Tracking User Activity
Understanding who is currently logged into a Windows 10 system is crucial for several reasons:
- Security: Tracking user activity helps identify potential unauthorized access, malicious activity, or breaches of security protocols.
- Resource Management: Monitoring active users allows for efficient allocation of system resources, preventing bottlenecks and ensuring optimal performance.
- Accountability: Knowing who is using the system provides a clear audit trail, enabling administrators to trace actions and troubleshoot issues.
- Troubleshooting: Identifying active users can be instrumental in diagnosing software conflicts, application errors, or hardware malfunctions.
- Remote Management: For organizations with multiple workstations, tracking logged-in users facilitates remote administration and support.
Methods for Identifying Logged-in Users
Windows 10 offers a variety of methods to determine active users, each with its own advantages and limitations:
1. Taskbar:
- Visual Inspection: The taskbar, located at the bottom of the screen, displays the user account picture and name for the currently active user.
- Limitations: This method only identifies the primary user logged in, not other users potentially active in the system.
2. Task Manager:
- Process Overview: Accessing the Task Manager (Ctrl+Shift+Esc) provides a comprehensive list of running processes. The "Users" tab displays all active user accounts, including their login times and associated processes.
- Benefits: This method provides a detailed overview of user activity, including their associated processes and resource usage.
- Limitations: The Task Manager requires user access and does not reveal information about sessions initiated through remote access tools.
3. Command Prompt:
- "quser" Command: Using the command prompt, the "quser" command displays a list of currently logged-in users, their session IDs, and login times.
- Benefits: This method offers a concise and efficient way to identify logged-in users.
- Limitations: It requires user access and does not provide information about user activity beyond login details.
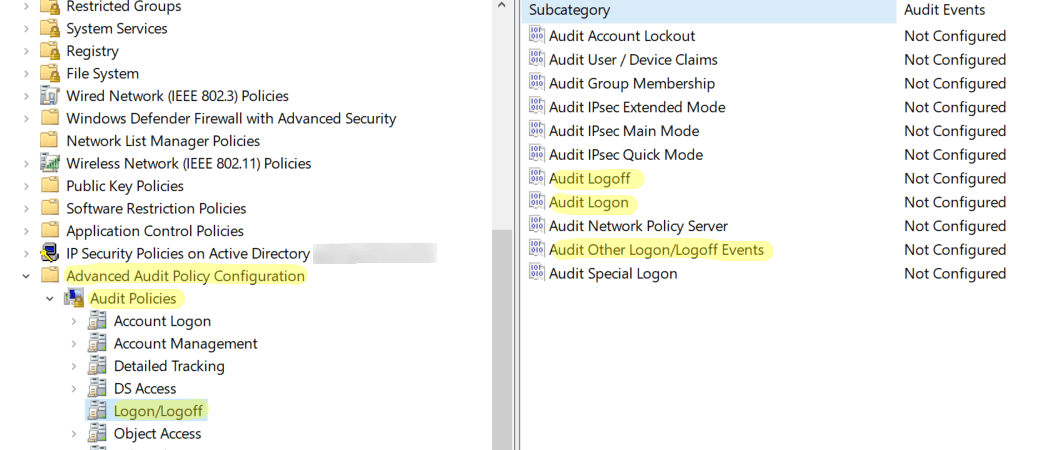
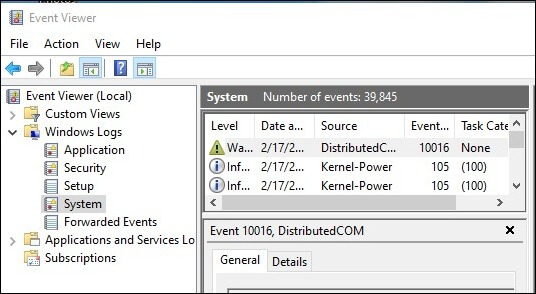
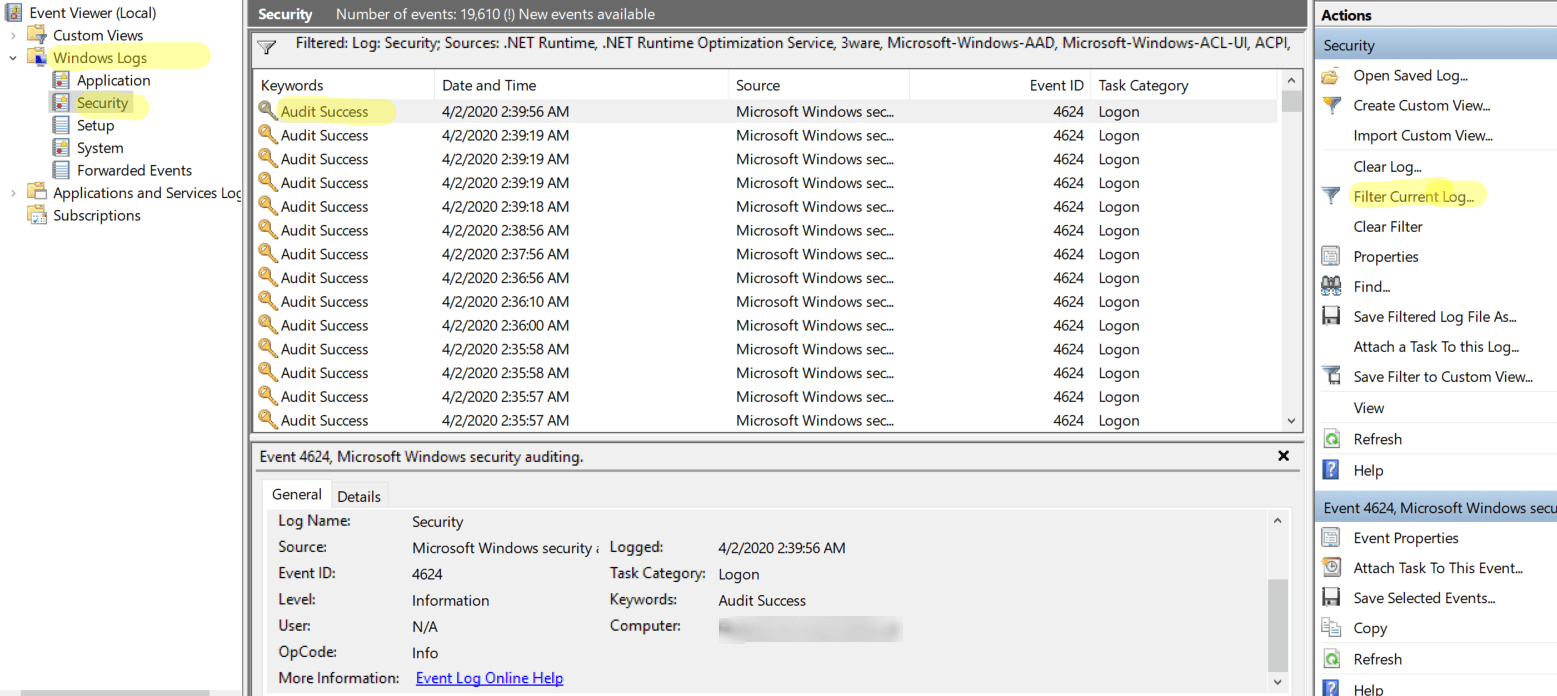
4. Event Viewer:
- Security Logs: The Event Viewer (accessible through the search bar) stores system events, including user logins and logouts. This provides a detailed historical record of user activity.
- Benefits: The Event Viewer offers a robust audit trail, capturing all user activity over time.
- Limitations: Navigating the Event Viewer requires familiarity with its structure and event types.
5. Remote Desktop Services:
- Server Manager: For organizations using Remote Desktop Services (RDS), the Server Manager provides a centralized view of all active user sessions on the RDS server.
- Benefits: This method offers a comprehensive overview of user activity across multiple remote sessions.
- Limitations: It requires access to the RDS server and is not applicable to individual workstations.
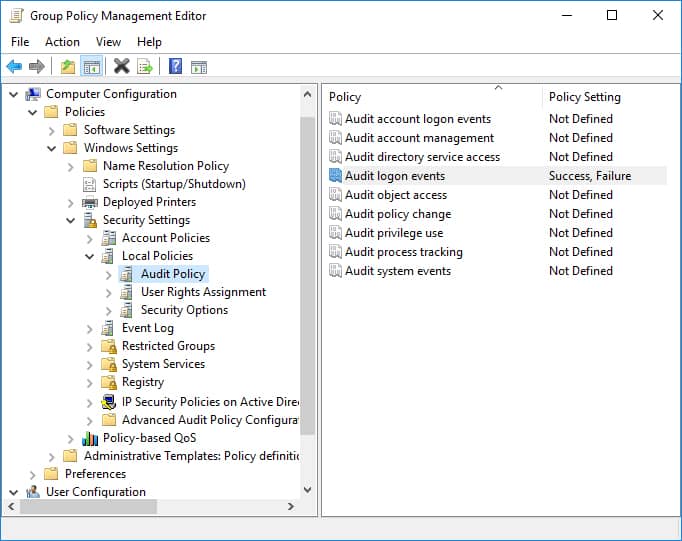
6. Group Policy:
- Audit Policies: Windows 10 allows administrators to configure audit policies to record specific user actions, such as login attempts, file access, and program execution.
- Benefits: This method enables granular monitoring of user activity based on specific policies.
- Limitations: Setting up and managing audit policies requires technical expertise.
Understanding User Activity: FAQs
1. What is the difference between a user being logged in and a user being active?
A user is considered "logged in" when their account is actively connected to the system, regardless of whether they are actively using the computer. Conversely, a user is considered "active" when they are actively interacting with the system, such as opening applications, accessing files, or using the keyboard or mouse.
2. Can I see what websites a user has visited?
Windows 10 does not inherently track website browsing history. However, specific browsers, such as Microsoft Edge or Chrome, may store browsing history, which can be accessed by the user or administrator.
3. How can I track user activity on a remote computer?
Remote monitoring tools, such as Microsoft’s Remote Desktop Services or third-party monitoring software, can be used to track user activity on remote computers.
4. How can I prevent unauthorized users from logging in?
Setting strong passwords, enabling multi-factor authentication, and configuring user account control settings can help prevent unauthorized logins.
5. How can I manage user permissions?
Windows 10 allows administrators to control user permissions through group policies and individual account settings. This ensures that users only have access to the resources they need.
Tips for Managing User Activity
1. Regularly review user activity logs: This helps identify potential security threats or performance issues.
2. Use strong passwords and enable multi-factor authentication: This helps prevent unauthorized access to user accounts.
3. Regularly update security software: This protects against malware and other threats.
4. Limit user privileges: Grant users only the permissions they need to perform their tasks.
5. Implement a robust backup strategy: This ensures that data is protected in case of system failure or data loss.
6. Educate users about security best practices: This helps prevent accidental breaches and promotes a secure computing environment.
Conclusion
Understanding user activity in Windows 10 is essential for maintaining security, managing resources, and ensuring system stability. By leveraging the various methods outlined in this guide, administrators can gain valuable insights into user behavior, identify potential issues, and implement appropriate security measures. Regularly monitoring and managing user activity is crucial for creating a secure and efficient computing environment.
Closure
Thus, we hope this article has provided valuable insights into Understanding User Activity in Windows 10: A Comprehensive Guide. We hope you find this article informative and beneficial. See you in our next article!